Security
Before making your web applications available for others to use, you should learn the basics of how to write secure applications, or else you and the visitors of your site will be vulnerable to hackers.
Injection attacks
Try adding a comment to your site with the author <h1>Evil Hacker</h1> and the message <script>alert("You've been hacked!");</script>. You should see a popup window and the comments should show the author in big letters.
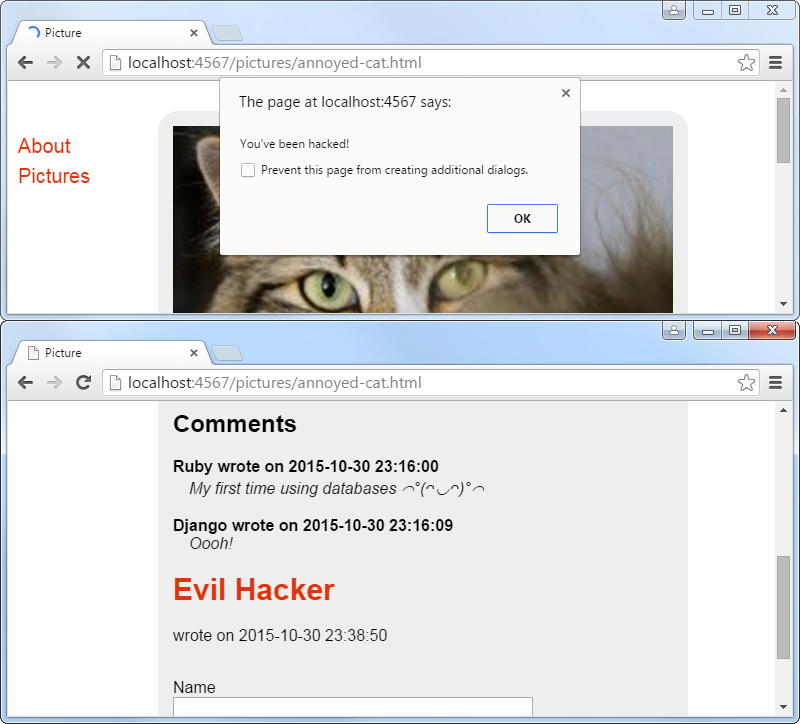
This is an example of a classical web application security flaw. The application takes input from the user and puts it as-is into a context where it can be interpreted as code. In the web browser the attack is called cross-site scripting (XSS) and in the database it is called SQL injection.
How to avoid
The solution to injection attacks is to always sanitize your input data. For example in HTML the < character needs to be replaced with < which the web browser will then show as < instead of interpreting it as the start of an HTML tag.
Escape explicitly
A common but inferior way is to explicitly escape the data at every place where it could be dangerous. For example in Sinatra you can create a helper method for calling escape_html, which you would then use in your templates like this:
<%= h scary_output %>
The problem with this approach is that if you forget it in even one place, your application will have a security hole.
Escape by default
A better way is to make the way of least effort also the secure way. In Sinatra you can escape all HTML automatically, so that every <%= scary_output %> is secure by default. For those cases where you actually need to inject HTML into a template, you can use the special form <%== html_on_purpose %> which won’t be escaped.
In app.rb, add the following code to the beginning of the file to enable HTML escaping by default.
require 'erubis'
set :erb, :escape_html => true
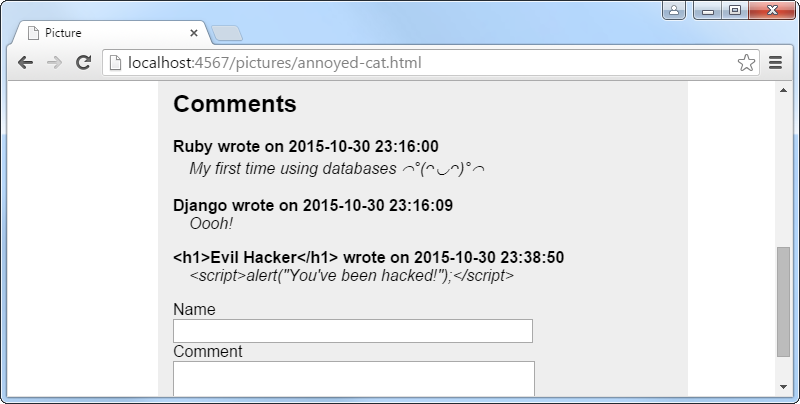
Have a look at the hacked picture page now. A bit too much was escaped, so in views/layout.erb you will need to disable escaping for the page content; replace <%= with <%==.
<%== yield %>
Now your web site is safe from the XSS attack.
OWASP Top 10
The OWASP Top 10 Project lists the ten most critical web application security risks and how to avoid them. The list has stayed mostly the same from year to year, so the industry as a whole has not learned to avoid these issues. If you learn them already now, before getting into the industry, maybe some day drops of water will make an ocean.
Proceed to the next chapter